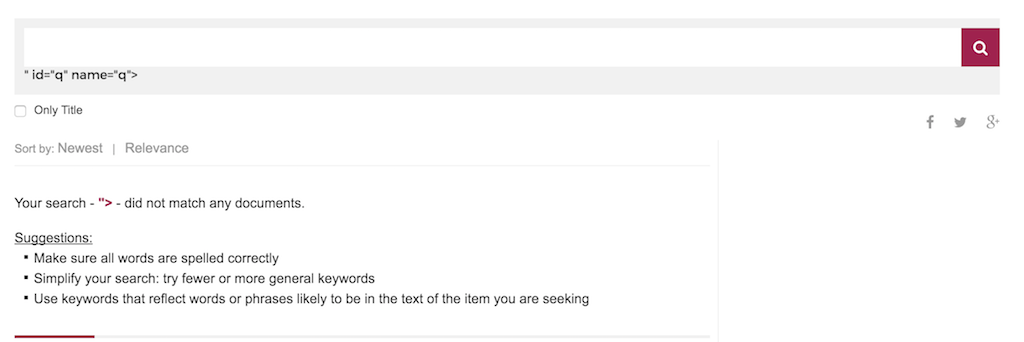
XSS on e.vnexpress.net
Recently I found two XSS vulnerabilities on vnExpress website. It all begins with the newly introduced English version of VnExpress, and I didn’t have to spend a lot of time to find the search box wasn’t escaped properly. Just do a search with “> will reveal this.
Pretty serious problem if anyone still doesn’t care about escaping user-input, especially on a search box. Luckily, a normal XSS payload will only works on Firefox, because Chrome and IE have XSS Auditor for a while now (you can still bypass it, which I will tell you later). Also because the site doesn’t have user account yet, the best I can do is launching a phishing attack (I jut did a PoC to demo what I can do, not really attack anyone).
[Read More]